Experts often use the terms PKI and digital certificates when explaining how digital signatures work. However, it can all get quite confusing for people who don’t have a technical background.
This article aims to clarify the role that public key cryptography, public key infrastructures (PKI), and digital certificates play in creating digital signatures.
The basics of public key cryptography
Public key cryptography uses a pair of keys to secure online communications and create digital signatures. Each party gets a private and public key. The two keys are different but mathematically related. As its name suggests, the private key must be kept secret. On the other hand, the public key can be shared with others.
An electronic message encrypted with a person’s public key can only be decrypted using the same person’s corresponding private key. Similarly, a digital signature created with a person’s private key can only be validated with the same person’s public key. Here’s how it works.
Ensuring the confidentiality of electronic messages
Let’s say Dan wants to send a confidential message to Stacey. He wants to ensure that Stacey is the only one who can read its contents, so he uses her public key to encrypt the message. The only way to decrypt the message is with Stacey’s corresponding private key. Since Stacey is the only one who knows her private key, Dan can be sure that no one else can read the message.
This is how public key cryptography ensures the confidentiality of electronic communications.
Creating digital signatures
For creating digital signatures, the process looks a little bit different.
Let’s say Dan sends Stacey a contract for signature. In this case, Stacey will use her private key to sign the document. Dan will then use Stacey’s public key to validate the signature. If Stacey’s public key can validate the signature, Stacey is the actual signer of the document.
This is how you can use public key cryptography to create a digital signature.
What are digital certificates?
A digital certificate is the digital equivalent of an ID card. Much like an ID card, a digital certificate can prove that a person or organization is who they say they are. Therefore, digital certificates are essential to ensure trust in public key cryptography.
Let’s go back to the example above. Without a digital certificate, Dan can’t be sure that the public key that was shared with him really belongs to Stacey. Matt could easily pose as Stacey, sharing his public and private key with Dan instead.
A digital certificate contains information on its owner’s identity and the owner’s public key, thus binding the owner to the public key.
Digital certificates are issued by trusted organizations called Certification Authorities. Before issuing a digital certificate, a CA verifies the identity of the person requesting the certificate to ensure they are who they claim to be.
Simply put, digital certificates serve as a means of authenticating an entity in public key encryption schemes.
Besides electronic document signing, digital certificates are commonly used for authentication purposes. Certificate-based authentication refers to the use of a digital certificate to verify the identity of an entity before allowing them to access a system, file, network, or application.
What about PKI?
A public key infrastructure is the set of policies, procedures, roles, and technologies needed to issue, manage, distribute, store, and revoke digital certificates in an encryption scheme based on public-key cryptography.
What are the types of digital certificates?
The three main types of digital certificates are:
1. TLS certificates
Transport Layer Security (TLS) is a cryptographic protocol that ensures the privacy and integrity of data sent over the Internet.
TLS certificates are data files containing information about the identity of a website’s owner as well as their public key. Besides making TLS encryption possible, TLS server certificates also authenticate the identity of a website’s owner.
Let’s say you want to make an online purchase and need to fill in your card information. Thanks to TLS, your payment details will be encrypted, and thus protected from prying eyes while in transit.
The URLs of websites secured with TLS certificates start with “HTTPS” instead of “HTTP” and a tiny padlock is displayed in front of these URLs in the address bar.
2. Code signing certificates
Developers use code signing certificates to digitally sign the code of their software. Code signing certificates bind the identity of the developer to the signed software and prevent code tampering. Therefore, digitally signed software is safer to download for the end-user.
Unfortunately, even though a signed software is more reliable than an unsigned one, it still can’t always be trusted.
Anyone can purchase a code signing certificate, even developers who purposely add malicious code in their applications. Therefore, you should make sure that you only download software signed by developers that you trust.
3. Client certificates
Client certificates allow remote servers to verify the identity of individual users or devices making a request.
Digital ID certificates are an example of client certificates. You can use these certificates to sign documents digitally and access online public services.
Benefits of signing documents using digital ID certificates:
- the signer of the document is who they say they are
- the signer’s identity is bound to the public key contained in the digital ID certificate, so they can’t deny the signature
What is a Certificate Authority (CA)?
A Certificate Authority (CA) is a company that, after being audited for compliance, has been authorized to issue digital certificates to entities.
In the EU, the eIDAS Regulation defines the requirements that Certificate Authorities must meet as Trust Service Providers (TSP) and Qualified Trust Service Providers (QTSP). You can access the complete list of Qualified Trust Service Providers as defined by eIDAS through the EU Trusted List browser.
Why should you trust authentication via digital certificates?
The main benefit of digital certificates is that they are issued by trusted authorities (Certificate Authorities). These authorities verify the identity of the requester before issuing the certificate.
Suppose you ask someone to sign a physical contract. You will first need to check their passport to verify their identity. If the passport is original, valid, and the photo ID matches, you will have verified the identity of that person.
Similarly, you can verify the identity of a person with the help of a digital certificate. However, instead of asking them to meet in person, you can ensure that the right person is signing the document remotely by using certificate-based digital signatures.
And just as you’d trust that a passport released by an official national department can identify a person safely, you can also trust that a digital certificate issued by a Certificate Authority securely identifies that person online.
When issuing the digital certificate, the Certificate Authority is responsible for verifying the identity of the person, using reliable identification methods defined in the eIDAS Regulation. For example, electronic IDs (such as MitID, BankID and itsme®) or smartphone apps capable of scanning the NFC chip in a passport and verifying the presence of the passport holder through face verification and liveliness checks.
Digital certificate example
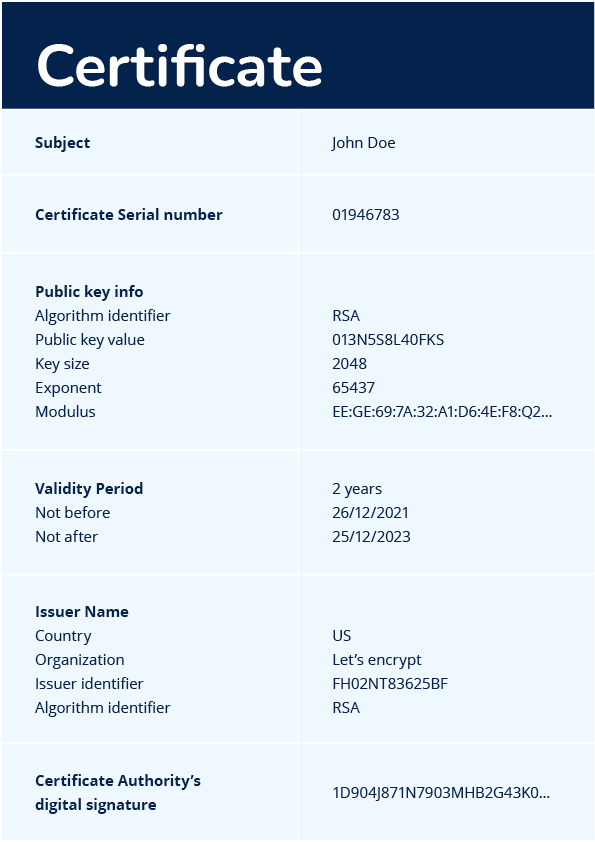
A digital certificate commonly includes information about:
- the identity of the certificate’s owner;
- the certificate owner’s public key;
- the certificate’s validity period;
- the trusted authority that issued the certificate.
Finally, it contains the digital signature of the certificate’s issuer.
What is the difference between a digital signature and a digital certificate?
The main difference is that a digital certificate binds an entity to its public key to authenticate them while a digital signature binds the signer to the provisions stated in the signed document.
Therefore, a digital certificate is used as proof of the signer’s identity when producing a digital signature for a document.
| Digital signature | Digital certificate | |
|---|---|---|
| What is it? | A very large number created using an algorithm | A digital file |
| What does it do? | Authenticates the signer’s identity and the integrity of signed messages | Authenticates the identity of the certificate owner |
| How is it created? | A document is run through a hashing algorithm to generate a hash called message digest. The message digest is then encrypted using the signer’s private key (by performing certain calculations). | Issued to an entity by a Certificate Authority (CA) (after verifying the entity’s identity) |
Digital certificates & Penneo
Penneo Sign enables document signing with Qualified, Advanced, and Simple Electronic Signatures, depending on the chosen signature method. Qualified and Advanced electronic signatures are based on digital certificates, whereas Simple Electronic Signatures are not certificate-based.
Some electronic IDs (eIDs) contain digital certificates, issued by the Certificate Authority of the provider. For example the itsme® app provides a qualified certificate to its users. When signing documents through Penneo, the user simply presents their certificate to Penneo through the itsme® app, and Penneo checks the validity of the certificate.
A signer can also identify themselves by authenticating with a valid eID, such as MitID, BankID Sweden, BankID Norway, or Finnish Bank IDs and Mobiilivarmenne. Based on the authentication, Penneo then acts as Certificate Authority, issuing a digital certificate to them for one-time use. The signer then completes the signing process using this one-time certificate.
Penneo also provides Simple Electronic Signatures, which are not certificate-based.





