Encryption helps companies and individuals protect their data from prying eyes. Many digital tools — from messaging apps to KYC software and document management systems — rely on encryption to keep their users’ data safe. In the case of digital signatures, encryption makes it possible to authenticate the signer with absolute certainty.
What is encryption?
Encryption is the process of converting electronic information into unreadable formats. It uses mathematical procedures, known as encryption algorithms, to ensure that only authorized parties can access the information.
You can protect both data in transit and data at rest with the help of encryption. Data in transit is data actively moving from the sender to the recipient. Conversely, data at rest is data stored on a device or network.
What about end-to-end encryption?
When people communicate online, the data doesn’t go directly from the sender to the recipient. Instead, it travels through servers before reaching its destination.
Many systems encrypt data before sending it to the server, decrypt it when it reaches the server, and encrypt it again before sending it to the recipient. Unfortunately, this means that the servers can see the data in its original form, leaving room for bad actors to access and exploit it.
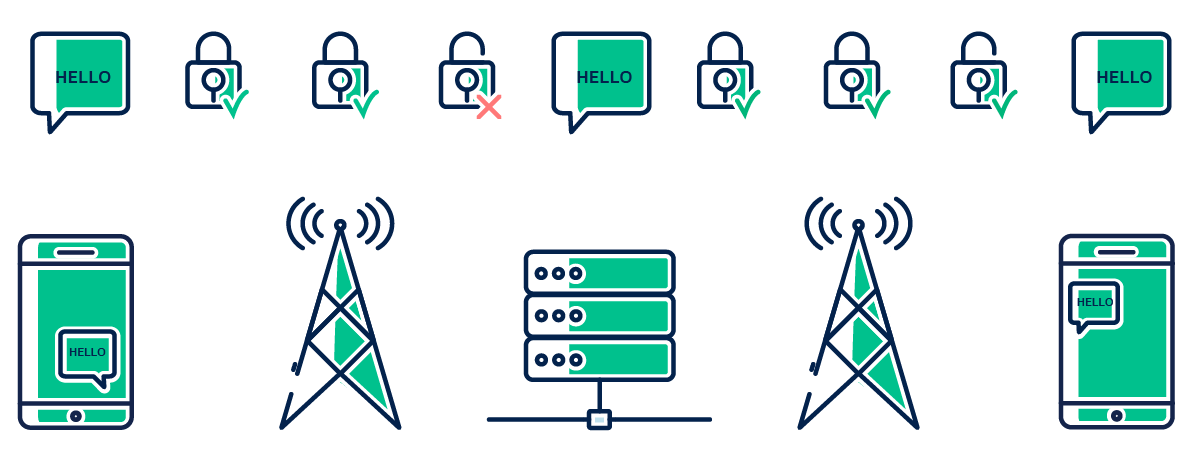
On the other hand, systems that use end-to-end encryption (E2EE) encrypt the data before transmitting it and only decrypt it once it reaches its intended recipient. As a result, servers can’t access the decrypted data anymore.
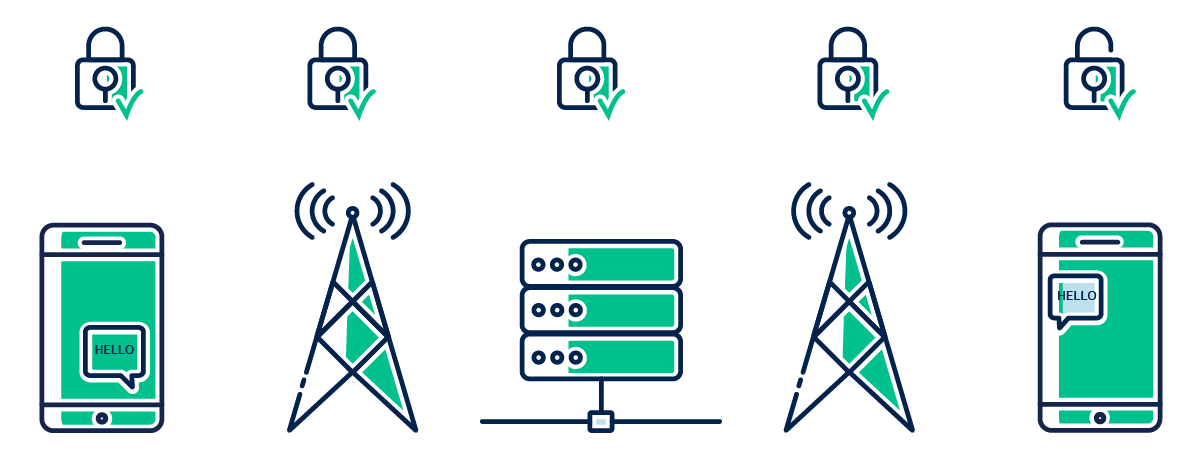
With E2EE, you can protect the confidentiality of your data exchanges from unauthorized third parties, including Internet service providers and communication service providers. Since only the intended recipient can decrypt end-to-end encrypted messages, E2EE is the most secure method of communicating online.
What are the two main types of encryption?
Based on the number of keys involved in the process, the main two types of encryption are symmetric and asymmetric encryption. In cryptography, keys are random strings of bits that encryption algorithms use to encrypt and decrypt electronic communications.
1. Symmetric encryption
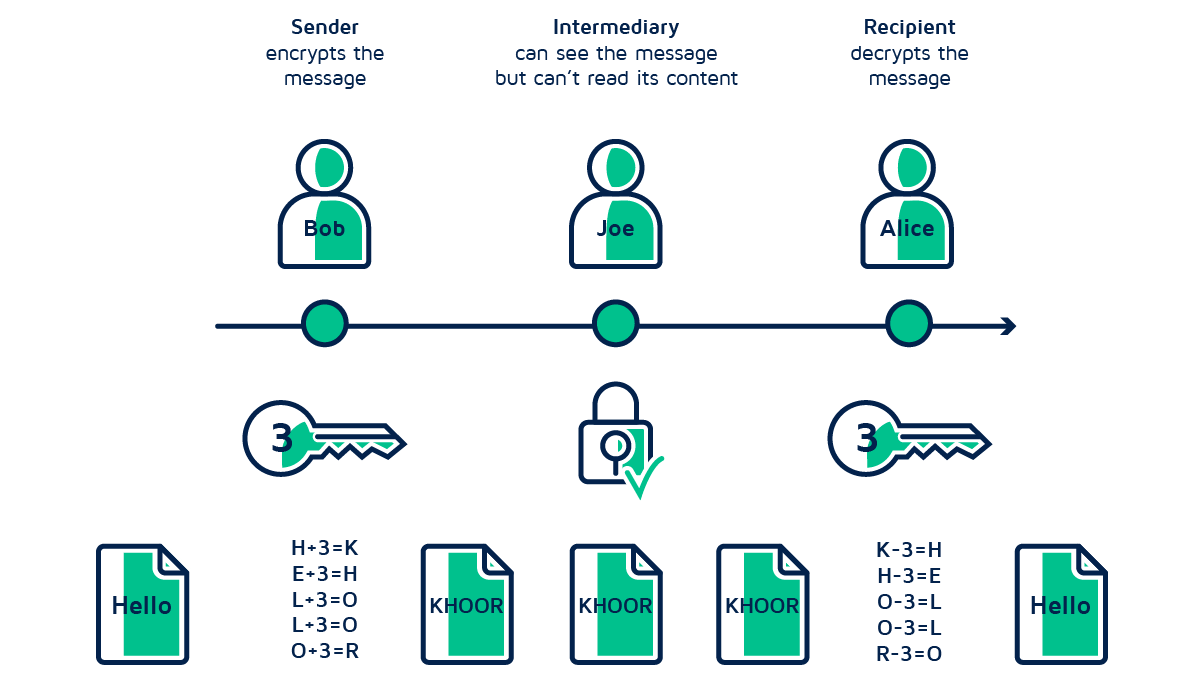
In this case, the sender and the recipient use a single key to encrypt and decrypt the message. Thus, they need to make sure that no one else except them has knowledge of the key.
Let’s say Bob wants to have a confidential conversation with Alice. The system generates a shared key that Bob uses to encrypt the message. Likewise, Alice uses the same key to decrypt it. No one else except Bob and Alice can make sense of the conversation since they are the only two people who know the key.
2. Asymmetric encryption
Asymmetric or public-key encryption involves two mathematically related keys — a public and a private key. Everyone can know your public key. However, you need to keep your private key to yourself.
Now, for Bob and Alice to have a private conversation, the system must generate two keys for each party. If Bob wants to send a private message to Alice, he uses her public key to encrypt it. Then, Alice uses her corresponding private key to decrypt it and read its contents.
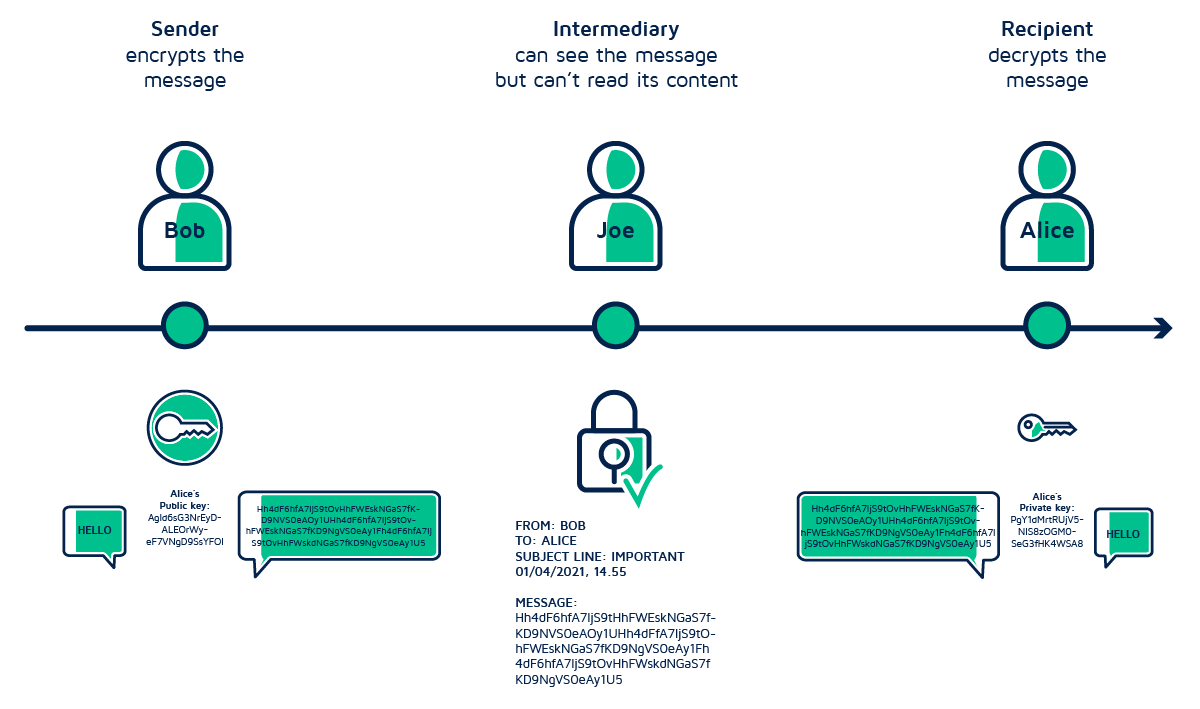
Similarly, when Alice writes back to Bob, she needs to use his public key to encrypt the reply. Bob can read her response by decrypting the message with his private key.
Since Alice and Bob are the only ones who have access to their private keys, no one else can eavesdrop on their conversation.
Besides preventing unauthorized access to confidential information and files, asymmetric encryption also enables the creation of valid digital signatures.
To create a digital signature, a person needs to sign the documents using their private key. Thus, anyone can verify the signer’s identity by decrypting the signature with the signer’s public key.
What are the benefits of encryption?
The benefits of encryption are many — from protecting data security and integrity to authenticating people who sign documents online.
-
- Data security: Encryption guards confidential information and files against data breaches. Breaking today’s encryption algorithms is practically impossible without knowing what key was used. Hence, cybercriminals and unauthorized third parties don’t have any way of restoring the data to its original form. It is therefore necessary to get an SSL certificate as it secures the data transition between the server and the browser. SSL brings 256-bit encryption to the table to keep cyber attackers away from the data
- Data integrity: Encrypting messages prevents hackers from intercepting and altering the documents and information you exchange online. Because they can’t understand the contents of electronic messages, bad actors have no way of tampering with them.
- Signer authentication: Due to public-key encryption, you can always authenticate the signers of electronic documents. Hence, you can always prove that a person signed a contract or agreement, even if they try to deny it.
- Regulatory compliance: Data protection is at the heart of the EU’s GDPR. Relying on systems that use encryption helps you comply with data protection regulations and avoid hefty fines in case of a breach.
- Customer trust: Customers do business with companies they trust. And today’s digital customers only trust companies that handle their data with the utmost care.
Does Penneo use encryption?
Both Penneo Sign and Penneo KYC use encryption to protect end users’ and customers’ information and documents.
Penneo Sign is a digital signing and data collection software that relies on asymmetric encryption to create digital signatures. Penneo encrypts stored data using AES-256, an algorithm that is practically unbreakable by brute force. Even though data transfers are not end-to-end encrypted by default, customers can enable E2EE for sensitive information and files.
Penneo KYC is a solution that automates the KYC process – from data collection and guided risk assessment to continuous data monitoring and record-keeping. Data and documents handled via Penneo KYC are end-to-end encrypted to ensure the highest level of security.





